CTrends GRC Platform
- Audit Management
- Risk Management
- Internal Control Monitoring
- Regulatory Compliance Management, etc.
Compliance with Bangladesh Bank (BB) for CAAT Software:
BB has revised its ICT Guideline for Banks and NBFI in 2023 where it imposed many new compliance requirements including audit automation. An excerpt from the ICT Security Guideline 2023 (v4.0) is given below:“2.4.3. The Organization shall use Computer-Assisted-Auditing Tools (CAATs) or a similar automated tool to perform IS audit planning, monitoring/auditing, control assessment, data extraction/analysis, fraud detection / prevention and management.”
This compliance can be easily achieved by deploying the CTrends GRC system. These products function differently. From the above clause, we see the need of three different products considering how products are built and marketed - Audit Management System (AMS), CAAT and Fraud Management System (FMS).
Though it is a compliance requirement on the banks and NBFIs, it is equally useful and beneficial for all the organizations trying to strengthen corporate governance. The key information about the CTrends GRC modules are given on this page.
CTrends Audit Management System (AMS)
Annual Audit Plan (AAP) Development:
This module allows the IA dept to maintain an audit universe and perform the AAP process in a risk-based audit approach. Both the auditors and the auditees
(selected management personnel) will use this same software for online collaboration.
The key features are as below:
- Maintain the auditable units covering process and compliance audits
- Maintain the risk assessment policy for branches and auditable units
- Conduct branch risk and auditable unit risk assessment
- Prepare AAP from the risk-assessed auditable units and branches
- Review, publishing, feedback and releasing the AAP
Individual Audit Engagements
The system allows audit team to conduct the individual audit engagements end-to-end.
The key features:
- Create very detailed risk-based audit work programs (AP) automatically for process and compliance audits
- Define the audit team and project schedule and assign responsibilities with timelines
- Create data request tracker (DRT), share data online and monitor the status
- Supervise and monitor the audit fieldwork, raise audit queries (AQM)
- Automated escalations on delays in each area of audit process
- Raising audit findings, rating, review, online feedback and finalisation
- Policy-based audit report rating
- Preparing audit reports, review, online feedback and finalisation, etc.
Audit Follow-up
After the audit reports are released, each assigned person for each finding post remediation update in the system. It brings efficiency and transparency.
Key features:
- Follow up on the open audit issues at the finger tips
- The respective auditees can claim the issue closure with evidence and the auditors can verify and close the findings with back and forth communications.
- Automated audit follow up dashboard and detailed reporting
- Revalidation audits with revised audit scores, etc.
Board Reporting
The internal audit (IA) departments are usually required to report summarized audit reports and work progress, compliance and control strength, etc.
at quarterly reviews and the year-end review. You can perform the whole process in the system considering that the report recipients may want to
review and give the feedback to the reports online.
Key features:
- Preparing quarterly BAC reports, review, online feedback and finalisation, etc.
- Preparing yearly BAC reports, review, online feedback and finalisation, etc.
Both internal audit team and external compliance audit teams can use this system to bring good practices and efficiency in auditing in a very coherent way.
The IC, RM & CM modules are integrated with the IA module.
The system has a parallel feature to conduct various branch audits based on predefined criteria. Multiple and independent criteria can be maintained.
We have already configured different audit criteria from the BB documentations. More can be defined. Key points:
- Maintain parallel branch audit criterial to perform simplified and branch audits.
- Configure audit criteria and score allocation policy
- Conduct branch audits from different perspectives such as operational controls, AML/CFT, foreign trade, etc.
- Audit score based comparative branch audit reporting for each perspective
- Printable audit reports in printer-friendly format
- Download from the system as PDF format and circulate the electronic copy.
Sustainability (ESG)
The system allows audit team to conduct the ESG risk assessment as an integral part of audit process.
The key features:
- Standard ESG metrics are already defined in the system.
- An ESG audit rating policy is also defined in the system following common practices.
- ESG risks can be included in the audit program, assessed and rated.
- Peridoc ESG risk / compliance rating can be conducted and becnhmarked.
CTrends CAAT Module
Computer Assisted Audit Technique (CAAT) is a specialized software designed for the auditors. This module is a generic auditing tool to automatically produce audit observations, which can be used to write audit findings. This is basically a data analysis tool designed to identify anomalies in transactions from auditors' angle. It reduces the work volume of auditors to complete the audit. This module is a generic transaction analysis tool while there are specific CAAT tools which directly produces audit reports. This module offers compliance analysis from the transactions which reside in this system (entire EBS).
- Purchase anomaly
- Payment anomaly
- Warehousing anomaly
- Sales anomaly
- Billing anomaly
- Accounting anomaly
- HR anomaly
- Payroll and income tax anomaly
- Loan disbursement process anomaly
- Cash deposit anomaly
- Cash withdrawal anomaly, etc.
In case transaction data reside in the external systems such as core banking system (CBS), ERP system (SAP / Oracle / others), you have to transfer the selected transactions to this system through API integration or manual data uploads. This part requires heavy system-level customization. CTrends has an ETL system to automatically transfer the data at specified intervals. For API level integration, the source system has to have the API in our prescribed output format. In case there is no API in the source system, CTrends team can develop once is database access is given.
This module does not produce the audit reports. The AMS module does. But it prepares the data sets for the auditors from the transactions with so many checks that audit time is greatly reduced and data accuracy is ensured. The success of this module depends on precise customization and timely data transfer.
CTrends Risk Management System (RM)
Risk Register and Risk-Control Matrix (RCM)
The system allows the Risk Management team (RMD) to identify, assess, remediate, monitor and react to business risks across all business functions.
The key features:
- Maintain risk classifications to organize the management of the business risks
- Maintain the database of business risks across all functions
- Already configured a comprehensive risk register of thousands of common business risks across Finance, Sales, Supply Chain, Production, Engineering, PMO, HR, IT, etc. The client just needs to review and learn them. It is a unique proposition for the client.
- New business risks can be defined
- The system allows RMD to define the remediation controls against each risk. The controls are taken from the Internal Control module (IC). You can assign risk owner to each business risk. It allows every user to easily find out which risks he/she is expected to manage. It is a risk treat plan in action and in detail.
Risk Assessment
The system allows the RMD to conduct full risk assessment process.
The key features:
- Define the risk assessment policy for likelihood, impact and risk level
- Define quarterly or half-yearly or yearly risk assessment based on the policy
- Generate risk assessment reports
- Visualizing risk exposure to business goals
- Visualizing risk exposure to functional goals
- Risk exposure to goals can be generated based on risk assessment or internal control assessment, etc.
Risk Monitoring
The system allows to monitor the movement of risks through the use of key risk indicators (KRIs).
The key features:
- Assign KRIs to risks from the internal library of thousands of predefined business metrics
- Post risk indicator data for those metrics which are produced in external systems
- See the KRI positions on the risk dashboard
- Get the risk intelligence from a risk map
- Link each risk to a functional goal and then to a central business goal
- Identify which goals of the business are more risky (unlikely) in achieving its target values, etc.
We have included hundreds of inherent functional risks which to support the clients to spend minimum efforts. We have also implemented the standard RCM and MAT. After defining a risk assessment policy, the users can conduct risk assessment and monitor the risks using KRI.
Management Action Trigger (MAT)
A MAT is a management action plan at specific positions of a business risk. Bangladesh Bank has imposed a requirement to develop and follow
MAT for the core business risks. This module is perfectly designed to achieve that requirement in an automated way. Please note that this
system comes with the seed data including the predefined risks and MATs which can be readily utilized. It is another great proposition for
the clients to use this software.
Basel-III
In the banking sector, the RMD team has to perform some processes to comply with the Basel-III Accord under the supervision of the central bank.
You can perform those processes here but you will need customization.
CTrends Regulatory Compliance Management System (CM)
Every organization needs to ensure compliance with the respective regulatory authority. Different authorities have different regulations and different compliance and reporting processes. Companies are observed to use different tools to organize their compliance management works. It increases cost and work volume. But this module enable the client to conduct all the compliance management works on the same platform.
Compliance Universe
Before you start working on the compliance management process, you have to configure each target compliance document in the system.
The key features:
- Configure each target regulation document in the system such as Acts, Rules, Authoritative guidelines, circulars, directives, etc.
- Write the implementation guideline and target output documents against each clause. This part needs expert knowledge of compliance managers which may be a bit difficult for the clients. We can help them to do this.
- Write the auditing procedure of each clause. The targeted output documents are considered as data requirements in auditing. This part needs expert knowledge of auditors which may be a bit difficult for the clients. We can help them to do this.
Compliance Projects
When the regulations are all configured, it is time to create implementation projects. The system will guide you to design the project. Every clause has to
be assigned to an employee with the action plans and timeline for each. When done, those assignments will automatically appear in their personal task dashboard.
The compliance calendar will show all the actions and time span. When they post work updates, the compliance dashboard will automatically be updated.
Compliance Assessment
The compliance team can undertake periodic compliance assessment of certain regulations. They have to create a project first and then conduct the assessments
under that project. Reporting is done against each compliance project.
Integration with Audit
These same regulation documents will be used by the audit module (IA) to create the audit work program. It saves a lot of time for the auditors. All regulations
are configured in the system in a way that the audit module understands its role in compliance auditing. It is another unique proposition for the client.
We have already configured the most common regulations of the BB, BTRC, ISO, SSC, etc. The following regulations are already configured to save the work volume of the client teams.
- BB: ICT Security Guideline 2023, CBS Guideline 2016, DCFCL, LDCL, DOS-10, Agent Banking Guideline, etc.
- SWIFT Customer Security Framework 2023
- PCI-DSS Standard
- ISO: 27001 (ISMS), 22301 (BCMS), 9001 (QMS), 20000-1 (SMS), 14001 (EMS), 22001 (FSMS), etc.
- PKI: CCA PKI Audit Guideline 2021, Interoperability Guideline 2021, WebTrust for CAs, Trust Services Principles for SOC2
- BTRC: Telecommunications Act 2001, MNO Cellular Phone Service Operator License, MNO Radio Communications Apparatus License, etc.
CTrends Internal Control Monitoring System (IC)
Internal control is an activity designed to prevent or detect or remediate a risk to the business. All the risk, compliance, audit and other governance professionals work on internal controls. Control activities are integral part of any business process which is well designed.
Internal Control Universe
Creation of the internal control activities with its details is the most critical factor of GRC success.
The key features:
- Define internal control classifications.
- Define control activity title, description, frequency, key attributes such as manual or automated, integrated, SOD control, DOA control, etc.
- Map each control to different international standards such as ISO, SOC2, SWIFT, PCI-DSS, TIA-942, CIS, GMP, GDP, etc.
- Define the control testing procedure and audit data requirements, etc.
Control Implementation Projects
When the controls are all configured, it is time to create implementation projects. Every control activity has to
be assigned to an employee with the action plans and timeline for each. When done, those assignments will automatically appear in their personal task dashboard.
When they post work updates, the compliance dashboard will automatically be updated.
In case where certain control activities are performed in other systems, the developers of those system can use our REST API to post control performance data
in this system. This module therefore shows a statement of control effectiveness based on artefacts of control performance.
Control Self-Assessment (CSA)
The auditors or management teams can undertake periodic control assessment of certain functions. They have to create a project first and then conduct the assessments
under that project. For this reason, the system allows to define an internal control maturity model. We have already configured the iCMM framework to do this
whole CSA work.
Each function can set quarterly or yearly control maturity targets and compare it with the assessed maturity at different time intervals.
Integration with Audit
These same regulation documents will be used by the audit module (IA) to create the audit work program. It saves a lot of time for the auditors. All regulations
are configured in the system in a way that the audit module understands its role in compliance auditing. It is another unique proposition for the client.
It enables the clients to maintain the complete database of all the internal activities of the entity. Control assessment and status monitoring across all functions makes it an ideal tool for ensuring an effective and strong internal control environment. We have used the iMinds iCMM control framework. As a result, thousands of internal control activities have been included in the system as seed data. It is a significant support to the clients.
Preconfigured Control Database
We have already configured thousands of common control activities across the following functions to drastically save client's time and effort. This is one
of the biggest propositions for the client.
- Sales & Marketing
- Customer Service
- Finance
- Supply Chain
- Engineering and Planning
- Manufacturing
- Project Management Office
- Information Technology
- General Banking
- Agent Banking
- Mobile Financial Services, etc.
CTrends Access Control Management System (AC)
User Identity Management
It is very important to understand and identify each user in the system. It is the usual practice to assign a human person to each user in the system.
But it is a common observation in IT audits that there are always users identified with no human person in a system or another. To prevent this whole
thing at the beginning, this system allows user creation only from employee master. Therefore, user identify verification is ensured for each user.
User Authentication
The system has a password-based authentication. There is a comprehensive password policy configuration panel to suit the client's policy.
- One-time password (OTP) for login - no admin support is needed.
- Password complexity
- Password aging and history
- Forbidden passwords, etc.
User Authorization
The user access cannot be given by the IT Admin. Each user has to apply for the needed UIs directly in the system as a self-service model.
Each access/privilege request has to go through a predefined approval workflow. When the last approval is conducted in the system, the user privileges
will automatically appear without any Admin's intervention. However, the user authorization can be limited with the following options.
- Role-based access control (RBAC)
- Host-based access control (HBAC)
- Time-based access control (TBAC)
- Location-based access control (LBAC)
User Audit Trail
The user audit trail is maintained by the system upon every interaction of the users. The audit trail is maintained with enough details to investigate
the incidents of interest. Each entry contains the user identity, action detail, timestamp, workstation identity (IP, hostname, browser), geo-location
(longitude, latitude), front-end type (browser or app), etc. The system has two types of audit trail reporting as below:
- Audit trail in a tabular model
- Audit trail on a map canvas
Security Override Documentation (SODD)
Sometime, some users may be required to have specific access which is usually against the established security policy. In such cases, the temporary
security control override is given to that user for a short period less than a year. When the matter is fixed, the override is withdrawn.
In this module, the SODD request, review, approval, tracking and reporting - the whole process can be performed.
The IT team can control and monitor the users' access to all application software, databases and server OS in the organization from a single point facilitating an online approval procedure.
Central User Database
In an organization, there are usually many business applications, databases and operating systems. Each one of them has a different user management
panel. Therefore, it is challenging to the IT security team to provision and deprovision user access in each system with every change in the user's
role changes. It leads to a common audit observation of finding user accounts in different systems which do not match with the user's role.
The client can use this system to manage user accounts and their privileges in all the business applications (having API or CLI facility of user management),
databases and operating systems in the organization. The Directory Server with SSO service may centralize the user database, but it does not identify
and record the application privileges.
Automated User Creation and Access Provisioning
All the systems have to be mirrored in this system for the user privileges at the implementation time. It is a comprehensive, very technical and one-time job.
In case of well known databases (Oracle, Postgres, SQL Server, etc.) and Operating Systems (Unix, Linux - Windows works differently),
only configurations will be enough. Otherwise, we have to deploy our access control gateway in each target system
to work as an agent. When the user access request is approved, the system automatically creates user accounts and privileges in the target system.
Automated User Removal
Similarly, when the user access is removed from this system, it automatically removes user accounts and privileges from the target system.
Therefore, the user access is totally synchronized across the organization. As this system has an HRMS product integrated with it, the employee separation
process can automatically revoke the user accounts and privileges associated with the exiting employee upon the release action.
Central User Access Reporting
The IT team can always report and monitor the user access in every system easily from the reporting options. This module works like a PAM system.
CTrends SOD Management System (SOD)
SOD is a vital control to fight fraud. It also eliminates chances of significant mistakes in the process. SOD is a preventive control.
We need to understand the fraud triangle first. The three points have to happen together for any fraud to take place – an opportunity
to commit fraud, a motivation or pressure to commit it and finally the person has to find out some rationale that s/he can get away with it.
Otherwise, the fraud doesn’t occur. There are several ways to prevent fraud.
The following common business processes are already configured in the system.
- Procurement Process (P2P)
- Vendor Payment (I2P)
- Inventory Process
- Sales Process (O2C)
- Billing Process
- Financial Close
- User Access Control, etc.
Business Process Configuration
SOD control is designed and deployed process by process. Therefore, it is important to define the business processes first. In this system, the client can define
the business processes in the Workflow (WF) module. We will just use them in this module to define the SOD matrix. The objective here is to reuse the business
processes across the modules to minimize configuration works and ensure better consistency.
SOD Matrix Configuration
The SOD matrix is automatically prepared from the user interfaces (system privileges) falling under the selected business process. The detailed understanding
of the business processes are covered in WF module.
- The matrix has two mirrored sides - one is active while the other is inactive.
- Mark the cells representing conflicting roles as specified in the row and column.
- Assign a risk rating of each conflict point as High / Medium / Low.
- Assign specific risks to each conflict point from the RM module.
- Assign specific controls to each conflict point from the IC module.
SOD Matrix Violation Reporting and Auditing
This module is a specialized CAAT meaning that it can produce audit results like an auditor.
- You can generate the SOD matrix for a business process which shows the number of conflicting users against each conflict points. From there, you can see the actual users who are having the conflicting roles (user interfaces in the system).
- You can directly generate the SOD audit report, print and sign - that much easy!
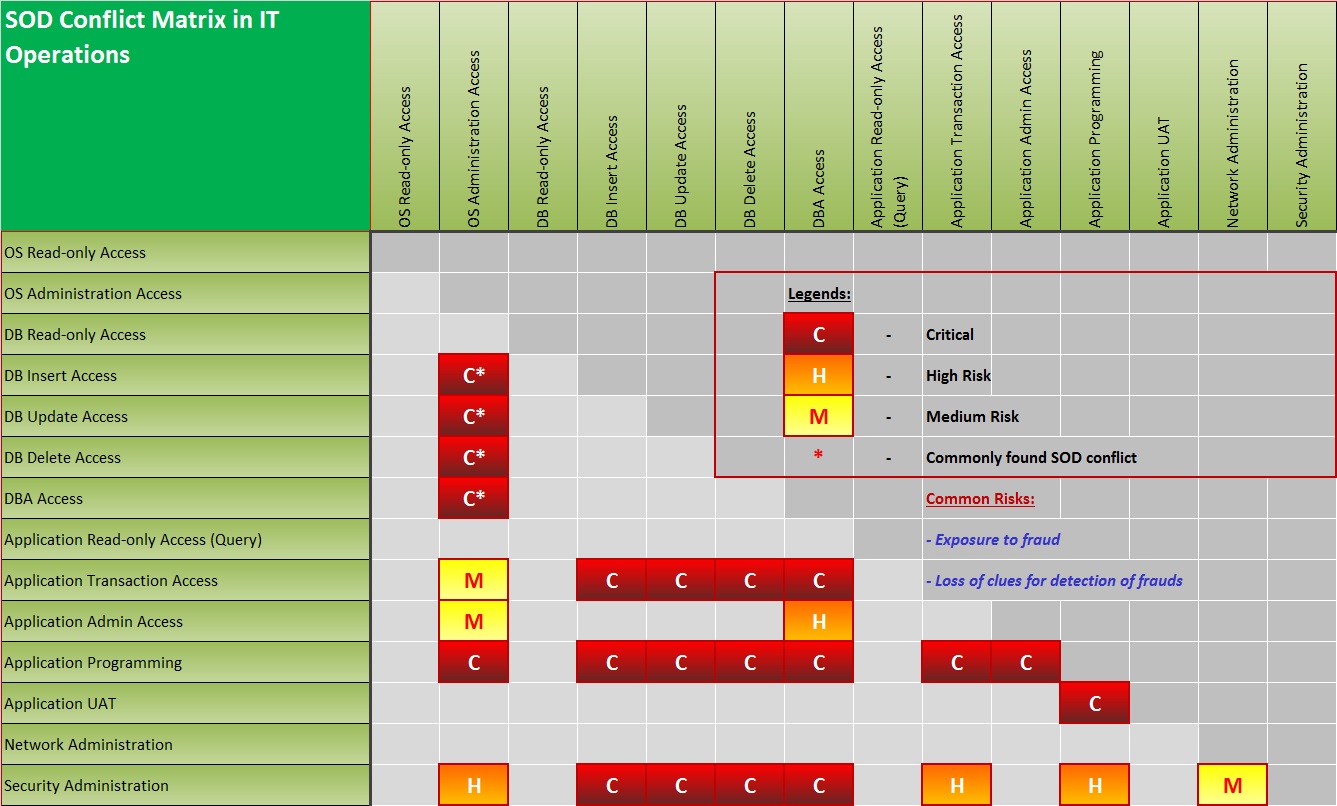
The clients can define the standard SOD conflict matrix for each business process. The Access Control module will use it to validate user access request. This module also produces SOD compliance audit reports automatically ready to sign.
Rationalization
To fight the development of fraud rationalization, the organization has to put examples of punishment or hard take-on to the fraudster.
Management is expected not to show different reactions to different persons for the same fraud committed. A consequent management policy (CMP)
can be defined to maintain uniformity. But, management generally doesn’t like to punish people.
Motivation
Motivation takes place in a person’s mind and can also happen in his or her private life outside the work environment or circle.
Therefore, it is not very easy to track people’s motivation level. However, clear code of conduct (CoC) and CMP should be developed
to teach the employees what is considered a prohibited act and what penalty may be given for doing a prohibited act. Then, CoC/CMP
training and compliance monitoring need to be performed periodically.
Opportunity
This is the key area to fight fraud. To prevent fraud in the first place, management has to focus on this area. This is the work processes and
resources together that can create an opportunity to commit a fraud. The three most effective management tools to prevent fraud are as below.
- Applying a proper segregation of duties (SOD)
- Establishing a proper delegation of authority
- Process automation, end-to-end.
CTrends Workflow Management System (WF)
Business Processes
A business process needs to be defined to facilitate different purposes in this platform such as SOD matrix definition, process audits, process quality
reporting, customer order status monitoring, etc. Therefore, we need to consider the following to configure a process.
- A unique process code and name to avoid confusion
- List of process steps. Here, only sequential process steps need to be define irrespective of their conditional branching in reality.
- Each step will be only a predefined business object and an action (usually CREATE - or EDIT where CREATE is not applicable)
- The right sequence of objects (steps)
- Section names to group the steps such as Procurement, Warehouse and Finance in a P2P process
- The approval workflow and TAT is configured at the object / action level which will automatically reflect on the business process.
Delegation of Authority (DOA)
In organizations, it is a common practice of delegating different authority levels to different levels of officials. Although the delegation is practiced,
in terms of principles, in all operational areas of operation, it is mostly practiced in approving expenses and payments. In the CTrends system,
all activities may be attached to a particular DOA, be it financial or operational. In the Workflow module, a DOA can be defined for every single
business object of a process, if the client wants. DOA will automatically be active in the corresponding business process. Different workflows for
review and approval can be assigned to different types of transactions and limits.
- The client can specify which business objects, e.g., RFP, PO, GRN, etc. will have approval workflows. Once specified, every transaction (create, edit, delete, etc.) of that object has to be approved online.
- Review and approval roles can be given to different persons in a workflow.
- Any number of persons can be included in the approval workflow.
- Different workflows can be created for different activity types of the same business object, e.g., create, edit, delete, etc.
- Different workflows can be maintained for different levels of transaction amounts
Process Quality Reporting
This module is designed considering the works of the QA professionals to monitor the process quality. When a process is defined, a standard time limit
is assigned to every step which adds up to the process TAT (turnaround time). The client can define a standard SLA value for every business process.
- SLA reports can be auto-generated for each business process using the workflow.
- SLA reports can be auto-generated (actual SLA vs. target SLA).
- The process automation scorecard (ASC) can be auto-generated. An ASC score above 75% indicates good reliability on the process for its continued enforcement.
- The process performance scorecard (PSC) can be auto-generated. A PSC score above 99% indicates satisfactory quality in the process outputs. Six Sigma principles can be considered to set the targets. However, this feature needs the QC rating on each process run.
Clients can configure approval workflow with approval limits as delegation level in the transactions to be made in the CTrends EBS suite (the base product of GRC system). Business processes can be designed here.
Business Objects
The entire EBS platform works with a logical control layer - we call it the business object (BO). Each BO represents a data set such as vendor invoice,
payment, employee, company, branch, location, etc. Each BO has specific predefined action types such as CREATE, EDIT, DELETE, BLOCK, APPROVE, CANCEL, etc.
Objects/Action are used to perform the following things:
- Approval workflow configuration
- Process SOD matrix configuration
- Business process steps
- Process turnaround time (TAT)
- A central definition of transaction types relevant to each object
- A central definition of document attachment to transaction types relevant to each object
- Common validation criteria for specific transaction types, etc.
Transaction Types
As a BO represents a business transaction data set, we need another layer to classify the transactions to apply different policies and controls.
We call it transaction types. We define the system wide transaction types against each BO. The corresponding transaction types will automatically
appear on the concerned transaction UI. The user will not have to do anything about it.
Objects Actions and System Privileges
Every user interface (UI) in the system is a system privilege and represents an activity such as create vendor invoice or edit invoice or delete invoice
or so. Therefore, each UI has a specific and unique ID in the system and is child of an object under a specific object action. For example, the system 6 UIs
to create audit assignments (AP) suitably designed for different types of audit to give a better user experience. But all of them technically fall under
one specific object and CREATE action.
CTrends Fraud Monitoring System (FMS)
An FMS application works based on fraud indicators (KFI). It uses statistical analysis and predictive analysis (AI). AI is gaining its popularity to identify suspected transactions. In both the cases, it needs the transactional data into this system. If the transaction occur in external systems, the time lag of transferring them into this system dominates the effectiveness of the FMS.
Automated KFI Assessment
The FMS gathers data from multiple sources, such as transaction history, customer data, and account activity.
The FMS uses algorithms and machine learning to analyze the data and identify suspicious patterns. FMSs use statistical analysis and predictive modeling to
compare current activity to normal patterns.
In this system, you have thousands of preconfigured business metrics, some of which can be used as KFI. When those metrics are updated, specific fraud alerts
can be raised by the system automatically. Apart from this trigger, transaction based algorithm can also be defined.
Similarity with Risk MAT
In this risk management module (RM), there is a methodology, called management action tigger (MAT), which are basically management action plans for
specific positions of the KRIs. There is a similar fraud lead triggers based on specific position of the KFIs.
Training Models for AI
In case you want to use the AI technology for FMS, the primary dependency will be training the ML models using actual fraud transactions. The training
process is automated, but inputting the actual fraud transactions will need to be manually selected. Moreover, the more such fraud transactions are
inputted to the FMS, the better it can identify the suspected frauds, which is basically self-contradictory. This problem can be solved by keeping the
training inputs independent of the actual transactions - just a separate inputting process (uploads) and collecting fraudulent transactions from external sources.
Fraud Lead Management
When a fraud lead (suspected fraud incident) is recorded manually or automatically by the system, it has to go the following steps in the system.
- Documenting the fraud lead (suspected or reported fraud)
- Verification of the lead
- Documenting the action plan
- Documenting the fraud scheme used as a lesson learned
- Updating the status of the action plan up to closure or dropping
